source-code-vulnerability-detection-project
Project maintained by DanielJRamirez Hosted on GitHub Pages — Theme by mattgraham
Source Code Vulnerability Detection
Abstract
In order to better understand and compare the techniques that are being developed to detect vulnerabilities in source codes, eight papers were selected to be researched and five were implemented. These papers each present different methods and operate on varying datasets and languages, however a selection of common metrics allows for adequate comparisons in their efficacy. This comparison helps to showcase the most successful individual strategies and overall implementations that can be applied to detect flaws in software.
Methods Researched
- On using distributed representations of source code for the detection of C security vulnerabilities
- Detecting Vulnerability in Source Code Using CNN and LSTM Network
- Devign: Effective Vulnerability Identification by Learning Comprehensive Program Semantics via Graph Neural Networks
- Automated Vulnerability Detection in Source Code Using Deep Representation Learning
- How to Detect Software Vulnerabilities in Source Code Using Machine Learning
- An Automatic Source Code Vulnerability Detection Approach Based on KELM
- SySeVR: A Framework for Using Deep Learning to Detect Software Vulnerabilities
- VUDENC: Vulnerability Detection with Deep Learning on a Natural Codebase for Python
Methods Implemented
- On using distributed representations of source code for the detection of C security vulnerabilities (repo) (our implementation)
- Devign: Effective Vulnerability Identification by Learning Comprehensive Program Semantics via Graph Neural Networks (repo) (our implementation)
- Automated Vulnerability Detection in Source Code Using Deep Representation Learning (repo) (our implementation)
- How to Detect Software Vulnerabilities in Source Code Using Machine Learning (repo) (our implementation)
- VUDENC: Vulnerability Detection with Deep Learning on a Natural Codebase for Python (repo) (our implementation)
Results
Figure 1. Accuracies across Methods
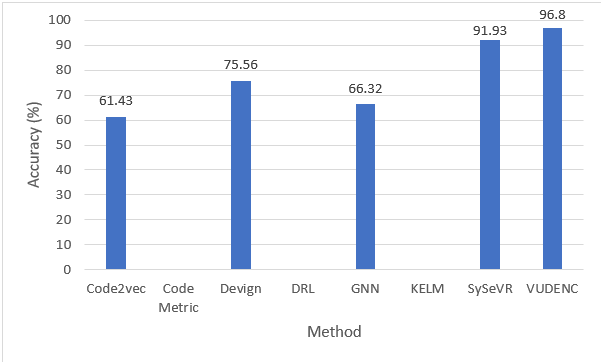
Figure 2. Precision and F1 Scores across Methods
